Answer-1:
Here to complete this task provided in this Communication network assignment we need to convert given binary stream into an analog waveform using the various modulation technique. The analog modulation is used in transmission of analog baseband signals. There are various modulation techniques are used for the analog modulation like amplitude modulation, frequency modulation, and phase modulation. Here these all techniques are used for the modulation of binary data “110101”. Hence by using the various frequency level of carrier signal the data would be modulated and then sends it towards the destination. So the modulation process by using the various frequency and modulation technique is shown in below screenshot:
Here to complete this task provided in this Communication network assignment we need to convert given binary stream into an analog waveform using the various modulation technique. The analog modulation is used in transmission of analog baseband signals. There are various modulation techniques are used for the analog modulation like amplitude modulation, frequency modulation, and phase modulation. Here these all techniques are used for the modulation of binary data “110101”. Hence by using the various frequency level of carrier signal the data would be modulated and then sends it towards the destination. So the modulation process by using the various frequency and modulation technique is shown in below screenshot:
Two-level Amplitude Shift Keying
Two-level Frequency Shift Keying
Two-level Phase Shift Keying
Differential Phase Shift Keying
Four level Amplitude Shift Keying
Four level Amplitude Shift Keying
Eight level Amplitude Shift Keying
Answer – 2:
The multiple frequency shifts keying modulation process is used to transmit information signals over the network. The MFSK is required two or more frequency signals for the modulation of information signal. MFSK standard state working is on the basis of narrow tone or low-frequency modulation methodology. While we using MFSK modulation for the analog signal at that time it gives modulated signal as high frequency instead of positive bits or 1’s and it provides the lower frequency signal instead of negative bits or 0’s. By using the MFKS technique it can able to provide the various features like lower error rate, high noise rejection, multipath rejection, and better sensitivity, etc. There are some drawbacks of MFSK which makes complex tuning, offset value of transmission and receiver is low, etc.
The multiple frequency shifts keying modulation process is used to transmit information signals over the network. The MFSK is required two or more frequency signals for the modulation of information signal. MFSK standard state working is on the basis of narrow tone or low-frequency modulation methodology. While we using MFSK modulation for the analog signal at that time it gives modulated signal as high frequency instead of positive bits or 1’s and it provides the lower frequency signal instead of negative bits or 0’s. By using the MFKS technique it can able to provide the various features like lower error rate, high noise rejection, multipath rejection, and better sensitivity, etc. There are some drawbacks of MFSK which makes complex tuning, offset value of transmission and receiver is low, etc.
Hence after discussion of the MFSK modulation technique in this Communication network assignment here we compute some modulated signal for the four-bit data combination. While us using the four-bit data combination then we get 16 different possibilities of data transmission over the network. As now as per the requirement MFSK modulation for the Fc = 1000 KHz, Fd = 50 KHz, and M = 16 is shown by below screenshot:
Answer -3:
There was amplitude modulation or frequency modulation is methodology is used as a modulation technique in this task. While the amplitude modulation is done then the modulating signal parameters change with respect to the amplitude of the signal. The frequency modulation techniques change the frequency parameters during the modulation. The below screenshots provided in this Communication network assignment shows amplitude modulation and frequency modulation of given signal:
There was amplitude modulation or frequency modulation is methodology is used as a modulation technique in this task. While the amplitude modulation is done then the modulating signal parameters change with respect to the amplitude of the signal. The frequency modulation techniques change the frequency parameters during the modulation. The below screenshots provided in this Communication network assignment shows amplitude modulation and frequency modulation of given signal:
Amplitude modulation:
Frequency modulation:
Answer – 4:
The QAM process is the same as the superimposing process of ASK modulation. There is two types of QAM technique present like M-QAM and standard QAM. The M-QAM provides much better results than standard QAM but as per the simplicity of standard QAM it was highly useful in communication. In M-QAM methodology M is used to represent the number of error bits detection in network. Usually M-bits are achieved by doing the converting process of data stream into Gray Code. The Karnaugh Maps is used to represent the QAM constellation output. Below we mention the calculation process to generate 16-QAM constellation.
The QAM process is the same as the superimposing process of ASK modulation. There is two types of QAM technique present like M-QAM and standard QAM. The M-QAM provides much better results than standard QAM but as per the simplicity of standard QAM it was highly useful in communication. In M-QAM methodology M is used to represent the number of error bits detection in network. Usually M-bits are achieved by doing the converting process of data stream into Gray Code. The Karnaugh Maps is used to represent the QAM constellation output. Below we mention the calculation process to generate 16-QAM constellation.
Now here to generate the 16-QAM there is 4 different amplitude level and 4 different phase level is used. So for that used amplitude and phase level values are {-3, -1, 1, 3}. Hence to draw the 16-QAM with the 4 ASK and PSK there is 4-bit K-map is used which is mention in below table:
AB/CD
|
-3
|
-1
|
1
|
3
|
-3
|
0000
|
0001
|
0011
|
0010
|
-1
|
0100
|
0101
|
0111
|
0110
|
1
|
1100
|
1101
|
1111
|
1110
|
3
|
1000
|
1001
|
1011
|
1010
|
Now as per the theory of array indication there is a need to relate the value of K-map with the effective value of array. So the array table with K-map value is as per below:
Number
|
Array value in binary
|
Array value
|
0
|
0000
|
-3-3j
|
1
|
0001
|
-3-1j
|
2
|
0010
|
-3+3j
|
3
|
0011
|
-3+1j
|
4
|
0100
|
-1-3j
|
5
|
0101
|
-1-1j
|
6
|
0110
|
-1+3j
|
7
|
0111
|
-1+1j
|
8
|
1000
|
+3-3j
|
9
|
1001
|
+3-1j
|
10
|
1010
|
+3+3j
|
11
|
1011
|
+3+1j
|
12
|
1100
|
+1-3j
|
13
|
1101
|
+1-1j
|
14
|
1110
|
+1+3j
|
15
|
1111
|
+1+1j
|
Once the Array table is created then it is required to plot the value of the binary related to the array value in the graph. So that the below screenshot shows the graph of 16-QAM constellation:
Answer – 5:
The signal transmitted over the communication network would be received with an error at the receiver due to some noise signal. While the information signal is coming with a one-bit error then it completely lose data because it changes all information in wrong direction. So that it is necessary to check the error in receiving signals. There are various techniques are used for the error check in the network like CRC, hamming code, etc. here we discuss the CRC error detection method:
The signal transmitted over the communication network would be received with an error at the receiver due to some noise signal. While the information signal is coming with a one-bit error then it completely lose data because it changes all information in wrong direction. So that it is necessary to check the error in receiving signals. There are various techniques are used for the error check in the network like CRC, hamming code, etc. here we discuss the CRC error detection method:
The cyclic redundancy check method is work on the principle of parity bit generalization. In this methodology there are parity bit was attached at the end of information bit string by sender and at the receiver end these bit are used for the verification of data integrity. The CRC is used for the short-range of an information signal to check the error like there is maximum 12000 bits limitation for the error check. There are various kinds of errors are detected by the CRC like singe bit error and burst error. The CRC parity implementation and error checking process over the network is mention by below screenshot:
The above snapshot provides the details information about the CRC error checking code at the sender and receiver side. Now as per the screenshot first data with some 0 bits are divided with help of CRC code pattern. Once the binary division process is complete then the reminder bits are known as per CRC bits or parity bits. After that the data will send in the pattern of data information and then CRC bits.
Now at the receiver end, the data with CRC bit would be divided with same divider bits and check reminder bits. After completion of the division process if reminder is zero then data would be accepted and reminder is not zero then data would be rejected by receiver. So these are steps that are required to do for error check using CRC code.
Answer – 6:
Now as per the above discussion of the CRC check methodology in a task we check error of transmitted data or integrity of data. So for that here given information bits are 111010110 and code pattern is 101110. The CRC check calculation is shown by the below screenshot:
Now as per the above discussion of the CRC check methodology in a task we check error of transmitted data or integrity of data. So for that here given information bits are 111010110 and code pattern is 101110. The CRC check calculation is shown by the below screenshot:
Now after the completion of CRC calculation at the sender side the transmitted data over the internet is 1110101101100. Now after that at receiver end CRC calculation is as per below screenshot:
So after completion of the calculation, the remainder of division is 1010. So we can say that the data should have some error bits and so receiver rejects this information data.
Answer – 7:
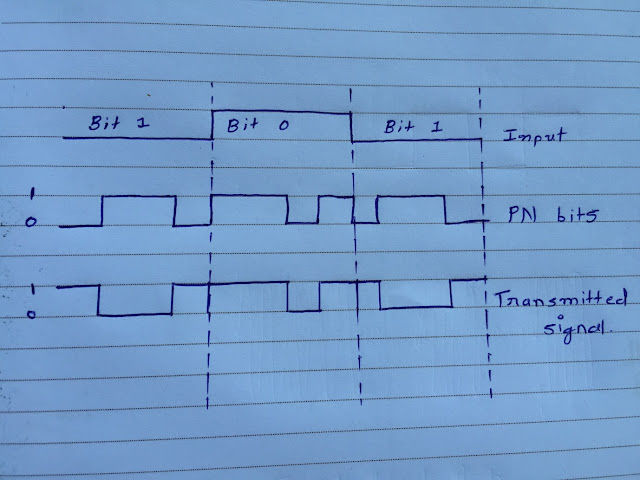
The direct sequence spread spectrum is used for data transmission over various bandwidth of transmitting waves. The process of data signal multiplication is completed through a chip code data stream that is generated via XOR operation. The chip-code data stream is able to represent the value of chips passing per second. The transmitted data signal combination of baseband carrier and information signal should provide wider bandwidth than original data stream. Hence at the receiver side there are CDMA demodulation process is occurring and then multiplying with the spread spectrum original signal will generated. These are some steps covered in DSSS. Now as per the given information below in this Communication network assignment we generate transmitted signal using DSSS:
The direct sequence spread spectrum is used for data transmission over various bandwidth of transmitting waves. The process of data signal multiplication is completed through a chip code data stream that is generated via XOR operation. The chip-code data stream is able to represent the value of chips passing per second. The transmitted data signal combination of baseband carrier and information signal should provide wider bandwidth than original data stream. Hence at the receiver side there are CDMA demodulation process is occurring and then multiplying with the spread spectrum original signal will generated. These are some steps covered in DSSS. Now as per the given information below in this Communication network assignment we generate transmitted signal using DSSS:
Input: 101 locally generated PN bit-stream: 011011010110 T=4Tc
Answer – 8:
The cellular network of any service provider needs to use the hexagonal cell structure for communication because as per the arrangement of hexagonal cell structure can be laid next to each other and there is no additional gap between two cells. Hence without making the gap or overlapping in structure it should able to cover all cellular networks. In hexagonal cell structure one base station was implemented the center cell structure and besides cell are able to communicate with separate frequency for each. Another base station configuration is as same as first one. There are six microcells are connected with the one base station. Now when we use circle or square cell structure at that time it is difficult to arrange the same design. The cell structure of the circle or square cell structure generates some overlapping or gap between two cells. So for that in gap area user cannot get network connectivity and in the case of the overlapping there are bandwidth migration is occurring and it is called noise. Now in square cell structure at the edge of cell user cannot get proper bandwidth due to large area or if we allocate sufficient bandwidth then cost of transmission would be increased. So for that we can say that hexagonal cell structure gives better output then circle and square cell structure. Below images shows the cell structure for hexagonal, circle and square cells:
The cellular network of any service provider needs to use the hexagonal cell structure for communication because as per the arrangement of hexagonal cell structure can be laid next to each other and there is no additional gap between two cells. Hence without making the gap or overlapping in structure it should able to cover all cellular networks. In hexagonal cell structure one base station was implemented the center cell structure and besides cell are able to communicate with separate frequency for each. Another base station configuration is as same as first one. There are six microcells are connected with the one base station. Now when we use circle or square cell structure at that time it is difficult to arrange the same design. The cell structure of the circle or square cell structure generates some overlapping or gap between two cells. So for that in gap area user cannot get network connectivity and in the case of the overlapping there are bandwidth migration is occurring and it is called noise. Now in square cell structure at the edge of cell user cannot get proper bandwidth due to large area or if we allocate sufficient bandwidth then cost of transmission would be increased. So for that we can say that hexagonal cell structure gives better output then circle and square cell structure. Below images shows the cell structure for hexagonal, circle and square cells:
Hexagonal cell structure:
Circle cell structure:
Square cell structure:
Reference:
Constructing a rectangular constellation for 16-QAM. (2015, June 4). Retrieved from https://www.gaussianwaves.com/2012/10/constructing-a-rectangular-constellation-for-16-qam/
DSSS. (n.d.). Retrieved from https://www.sciencedirect.com/topics/engineering/direct-sequence-spread-spectrum
Error Detection in Computer Networks. (2019, August 12). Retrieved from https://www.geeksforgeeks.org/error-detection-in-computer-networks/
Modulation, Analog modulation, Digital modulation, AM, FM, PM, ASK, FSK, PSK explained.
(n.d.). Communication network assignment Retrieved from http://www.equestionanswers.com/notes/modulation-analog-digital.php
Spread Spectrum Modulation. (n.d.). Retrieved from https://www.tutorialspoint.com/digital_communication/digital_communication_spread_spectrum_modulation.htm
Thakur, D. (n.d.). Cyclic Redundancy Check (CRC). Retrieved from http://ecomputernotes.com/computernetworkingnotes/communication-networks/cyclic-redundancy-check





























This might be the right article to get some science assignment help. Hope to see more from you.
ReplyDeleteWhenever you order from Assignmentworkhelp, you are guaranteed to receive only original college assignments, done by the best assignment writers. You are being assured to book your order now
ReplyDeleteonline assignment help